NuCypher (NKMS) Review- The SSL/TLS of Decentralized Applications
| Coin Name | NuCypher |
| Coin Ticker | NKMS |
| Token Type | ERC20 |
| Total Tokens | TBA |
| Website URL | https://www.nucypher.com/ |
| White Paper URL | https://www.nucypher.com/whitepapers/english.pdf |
Nucypher addresses the challenge of sharing sensitive data in both decentralized and centralized applications with a decentralized Key Management System (KMS) that provides encryption and cryptographic access control through proxy re-encryption. Just as SSL/TLS are cryptographic protocols that provide communications security over a computer network, Nucypher’s KMS will allows secure file sharing over decentralized applications
Article Summary
- The Idea and the Team Behind Nucypher
- The Nucypher Technology
- The Nucypher Tokens
- The Nucypher Network
- The ICO
The Idea and the Team Behind Nucypher
Nucypher allows you to share data in otherwise public networks such as ipfs or s3 and to share it as scalably and as arbitrarily as possible. Sensitive information such as medical data is stored on the blockchain under a company’s own private keys, and allocation of the information is granted to anyone necessary, at scale, via proxy re-encryption.
Here is the usual scenario for transmitting private data in any public network. Let’s take an example from your encrypted files stored in Dropbox. To share files with someone, you’ll need to download them, decrypt them with your own key and then re-encrypt them with the public key of the person you want to share it with. Sharing these files at scales is a cumbersome and time-consuming process.
“What I can do with proxy re-encryption that’s much more elegant and secure than either of those alternatives is I can basically delegate access to my encrypted data to someone else’s public key,” co-founder and CEO MacLane Wilkinson explains. How does this work? Nucypher created a re-encryption token off the public key of the person receiving the shared data. “The token can be shared with as many people as you like,” he adds.
The team includes two co-founders, MacLane Wilkison and Michael Egorov. MacLane, the CEO, is a former investment banker at Morgan Stanley with a background in software engineering while Michael, the company CTO, is a physicist and scientist from the Moscow Institute of Physics and Technology.
Nucypher is being used by a few companies, including MediBloc, an open-source healthcare data platform, and Datum, a decentralized NoSQL database backed by a blockchain ledger. In addition, Origin Protocol, a decentralized marketplace, will be using Nucypher for their sharing economy protocol.
The Nucypher Technology
Nucypher is a key management system (KMS) that provides a solution to the limitations of using consensus networks to securely store and manipulate private, encrypted data. A KMS doesn’t require trust from a centralized system.
The steps below demonstrate how Nucypher’s technology works with an example of sensitive data being shared between Alice and Bob:

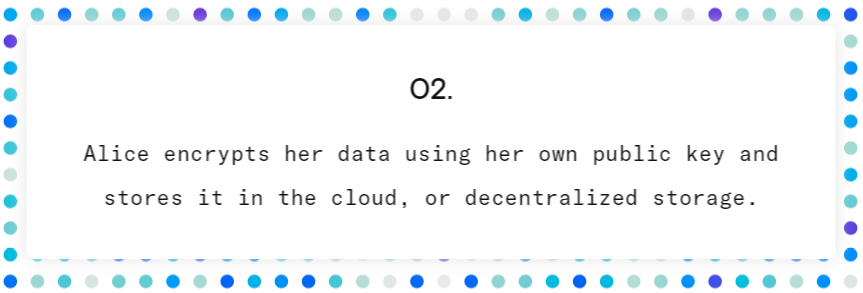


Although many vendors such as Amazon CloudHSM, Google Cloud KMS, Azure Key Vault and TrueVault offers KMS as a service, their centralized solutions are not suitable for organizations that want to share sensitive data and information and require a very high level of trust in the provider. Consensus networks seem to offer a good solution to this, but they put a lot of pressure on the network nodes. Nucypher’s solution is proxy re-encryption. It’s a bring-your-own-key (BYOK) model where private keys never leave the enterprise, and security controls and ensuring data can’t be accessed without authorization.
Nucypher’s technology has three main real-life applications:
- Cloud enablement — NuCypher allows enterprises to securely use cloud service providers such AWS by giving them a way to keep encryption keys in their own data centers and under their control. At the same tie, they don’t have to trust the crowd with their own encryption keys.
- Regulatory compliance — NuCypher is working with customers in the U.S. and Europe that need to comply with regulations such as HIPAA, PCI, GDPR and PSD2.
- Secure sharing of sensitive encrypted data — Enablement of seamless and secure data between organizations, whether it be it a customer, partner, supplier or even a regulator. The system’s segregation of the data and the encryption keys is critical, since it means that a regulator cannot subpoena the cloud provider to get their hands on the decrypted data.
The Nucypher Tokens (NUs)
The Nucypher token purpose is to distribute trust in the system. The amount of trust a person has in the system is represented by the number of tokens each node locks up.
On a practical level, Nucypher KMS tokens, or NUs, provide access to the re-encryption services. These tokens both reward miners for contributing and are also the price consumers pay to use the re-encryption services. NUs also provide an incentive to use the system correctly and securely, as opposed to using Ethers which do not provide that same security.
Miners can receive re-encryption keys based on the number of tokens they own. These tokens are held as a collateral deposit until activation of the keys, locked by a smart contract. Miners are paid by owners and users of the data for providing re-encryption services on the network and being available for re-encryption.
The Nucypher Network
Nucypher places prime importance on the ability to share data security in the public blockchain. Even with proxy re-encryption, the network still poses several security risks, but solutions are available for each risk.
- Pseudo-anonymity – First, re-encryption nodes should not have any idea of the data it is that they are re-encrypting. This pseudo-anonymity of the re-encryption keys prevents collusion between specific network participants to gain control of the data.
- Split-key re-encryption — Second, nodes are prevented from re-encrypting data immediately and not following guidelines of when to re-encrypt with a split-key proxy re-encryption scheme. Instead of one re-encryption key, several keys can be used to produce “re-encryption shares.”
- Challenge protocol – There is a risk of miners returning random numbers instead of the correctly re-encrypted data. However, these “fake” re-encryption keys designed to challenge the miners. The random numbers can be reported and proved to be a different result. The challengers can be awarded the miner’s collateral deposit as a result.
To start a re-encryption service, nodes must make a deposit to start a smart contract. Once the contract expires, the node can withdraw the deposit.
The ICO
Nucypher completed a $4.3 million presale for approximiately 30% of the initial tokens in the fall of 2017. The company hopes to reach mainnnet in the summer. After that, it will announce an ICO.
Nucypher has an approximate roadmap at this time that is not official.
“We’re taking a different approach from most projects in that we’re fully implementing the network prior to the public sale. In terms of (estimated) dates: testnet will be ready in a few weeks, 3rd party security audits are scheduled to begin in May, and mainnet will be ready sometime in the summer,” said MacLane in the Nucypher Telegram group.
